KEYTAKEAWAYS
- The RUNVM instruction vulnerability causes library corruption when a child VM exhausts gas, leaving the parent VM's libraries in a cleared state despite continued execution.
- TonBit demonstrated the vulnerability through a proof-of-concept test showing how XLOAD operations fail after RUNVM execution due to emptied libraries.
- As TON's Primary Security Assurance Provider, TonBit follows responsible disclosure practices and has submitted mitigation plans to the TON Foundation for patching.

CONTENT
TonBit security researchers discover critical non-atomic state transition vulnerability in TON Virtual Machine’s RUNVM instruction that corrupts library integrity when sub-VMs exhaust gas, potentially causing contract failures in dependent systems.
**Editorial content in partnership with TonBit. Views expressed do not reflect those of CoinRank. Not financial advice.
TonBit, under BitsLab, has once again unearthed a “time bomb” deep within the TON Virtual Machine (TVM) code—the non‑atomic state transition vulnerability in the RUNVM instruction. An attacker can exploit the moment when a sub‑VM exhausts its gas to corrupt the parent VM’s libraries and induce subsequent call failures, ultimately causing contracts that depend on library integrity to behave abnormally. Below, we retain the original technical details to present the full discovery and verification process for developers, helping the community gain an in‑depth understanding of the issue and bolster awareness of similar risks.
Below is the detailed description of the vulnerability:
The RUNVM instruction in TVM can pollute the caller’s state and render libraries unusable.
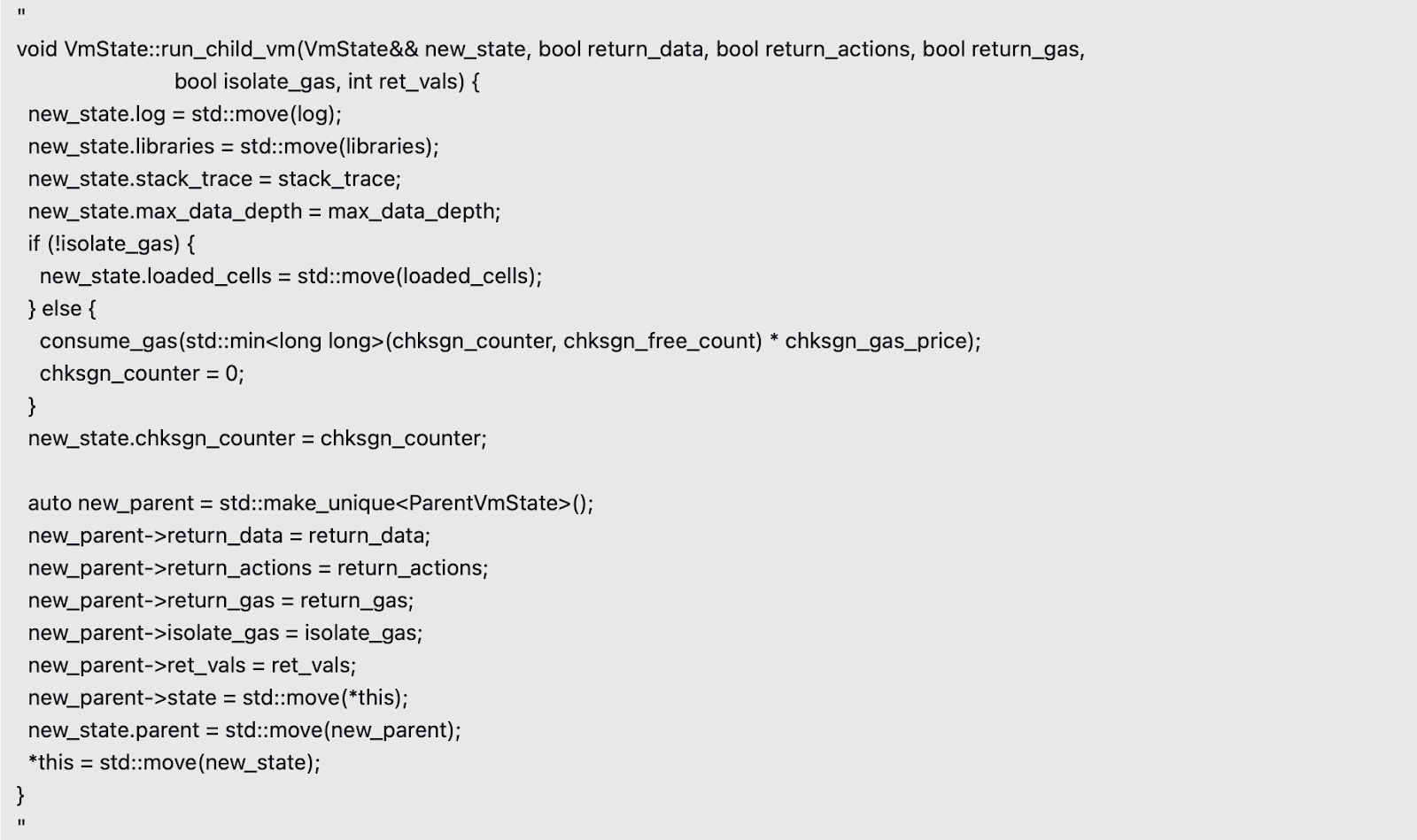
New vulnerability in the code of the ‘RUNVM’ instruction. It allows the caller’s state to be polluted. The relevant code snippet is as follows:
The code above is responsible for launching a child VM. It moves the ‘log’ and ‘libraries’ from the current VmState into a new VmState object ‘new_state’, and then replaces the current VmState with ‘new_state’.
The problem lies in the fact that this operation is not real atomic. Before the statement ‘*this = std::move(new_state);’ is executed, the VM might run out of gas and halt the process before ‘new_state’ replaces the current state. As a result, the ‘libraries’ may already have been moved out, leaving the child VM’s libraries in a cleared (moved) state.
Since the RUNVM instruction provides the isolate_gas parameter to isolate gas consumption between the child VM and the parent VM, this creates a scenario where:
Even when the child VM triggers a gas exhaustion exception, the parent VM still retains sufficient gas to continue execution. However, subsequent operations relying on ‘libraries’ will fail because the child VM has already moved/cleared them during the failed state transition. This leads to unexpected behavior in certain contracts that assume the integrity of the libraries.
PoC Verification:
We implemented the following test case to demonstrate this vulnerability:
Key Modifications for Testing:
To facilitate local observation of libraries state, we modified the NOP instruction to forcibly register a library entry:
Reproduction Steps:
Add this test case to crypto/test/vm.cpp
Run the test-vm executable
Observe the exception during XLOAD execution due to empty libraries。
Expected Behavior:
After NOP execution: libraries contain 1 entry
After RUNVMX execution, libraries become empty despite the parent VM continuation
XLOAD fails with an exception
This demonstrates how the non-atomic state transition, combined with gas isolation, creates an inconsistent state that violates execution context integrity.
This discovery once again highlights the deep expertise of TonBit, a subsidiary of BitsLab, in security research within the TON ecosystem. We have immediately submitted the technical details and mitigation plan to the TON Foundation and assisted in completing the remediation. We recommend that all developers promptly update their dependency libraries once the official patch is released; at the same time, incorporate more rigorous library‑integrity checks and gas‑management logic into custom contracts to prevent similar issues from being maliciously exploited. BitsLab will continue to uphold the principle of “responsible disclosure” and, together with the community, fortify the Web3 security perimeter.
ABOUT TONBIT
TonBit, a core sub-brand of BitsLab, is a trusted security expert and early builder within the TON ecosystem. As the Primary Security Assurance Provider (SAP) for the TON blockchain, TonBit specializes in comprehensive security audits, including Tact and FunC language audits, ensuring the integrity and resilience of projects built on TON. Officially endorsed by TON, TonBit has successfully audited numerous high-profile projects such as Catizen, Algebra, UTonic, Ton Batch Sender, TonUp, PixelSwap, Tradoor, Miniton, Thunder Finance, and nearly 20 other projects on TON, demonstrating its expertise in securing TON-based solutions.