KEYTAKEAWAYS
- Increased blockchain adoption has led to a rise in cyberattacks.
- Blockchain's open and trustless nature makes it vulnerable to both network attacks and application code vulnerabilities
- Robust security standards are essential for developing secure and adaptable dApps.
- Blockchain infrastructure security management involves a combination of both Web2 and Web3 security mitigation policies.

CONTENT
Explore the fundamentals of blockchain technology, its architectural components, and critical security considerations in this comprehensive guide to Web3 development and blockchain security.
Blockchain infrastructure has its own operational challenges, and cybersecurity is one of the most important amongst them all. While Web2 security policies are designed to deal with a centralised infrastructure, Web3 security policies have to be more accommodative of the various distributed elements of blockchain.
Key Talking Points:
- Technology Stack – Blockchain (Web3)
- Security challenges
- Conclusions
UNDERSTANDING BLOCKCHAIN FUNDAMENTALS
The growing popularity of blockchain, fuelled by its economic value, open-source nature, and the rise of alternative cryptocurrency-driven neo-financial systems, has made it a prime target for cybersecurity attacks.
The rapidly changing landscape of the crypto industry, combined with the decentralized and trustless structure of blockchain, requires a different approach to security, compliance, and risk management.
As blockchain security is a complex topic, this article will focus on the current security challenges we face. We will explore the different layers of blockchain technology, highlighting the security risks associated with each.
We’ll also have a look at some high-profile security breaches that have caused significant disruption in the blockchain space.
In a future article, we will revisit the topic to showcase some high-profile security breaches that have caused significant disruption in the blockchain space and explore the security measures and standards currently in place to protect blockchain networks.
Let’s explore.
WEB3 ARCHITECTURE & TECHNOLOGY STACK
For a better understanding of blockchain security concerns, let us give you a visual and logical perspective of the various technology stacks that drive the blockchain technology.
Blockchain technology is driven by several technology stacks that can be viewed as layers.
These interoperable layers of technology essentially offer various granular services that help achieve the larger blockchain functionality.
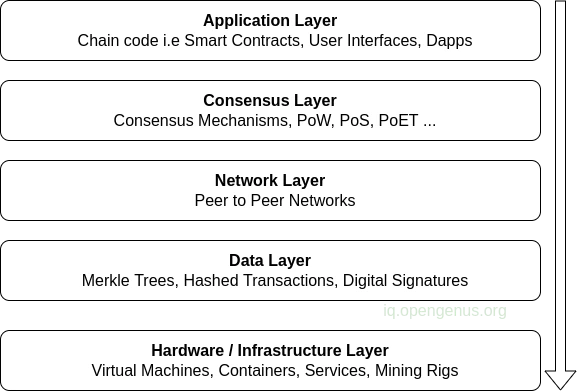
Blockchain Architecture can be principally viewed in the following layers:
1. Hardware Layer: This layer includes the software and hardware components necessary to run blockchain nodes and other essential elements. It encompasses server software, mining CPUs/GPUs for Bitcoin operations, blockchain protocols, and other infrastructure that supports the peer-to-peer (P2P) decentralized architecture of the blockchain.
2. Data Layer: Blockchain technology uses Distributed Ledger Technology (DLT) for secure data storage and access. The data layer is made up of various data management structures and models that enable DLT to ensure data security and decentralize data availability. Some of these data structuring methodologies utilise Merkel trees, hashing functions, digital signatures and others that are used to maintain data blocks in the blockchain.
3. Network Layer: The network layer provides interconnectivity amongst the various blockchain nodes. The network layers contain various protocols that oversee node discovery, blockchain state syncing, messaging and data exchange amongst the blockchain nodes. For, e.g.: Whisper and Swarm protocols are used for messaging and data exchange respectively in the Ethereum blockchain.
4. Consensus Layer: The consensus layer is essential for the functioning of blockchain platforms, whether it’s Ethereum, Hyperledger, or others. It validates and orders blocks while ensuring all participants are in agreement. This layer facilitates a set of agreements amongst nodes in the distributed peer-to-peer network, maintaining the decentralized and distributed nature of power.
5. Application Layer: The fourth layer of the blockchain architecture consists of application code that governs the blockchain. Some of these software elements consists of the chain code that contains all the consensus agreements and rules, communication protocol, encryption standards, file exchange protocols, and smart contracts (please see our other article on smart contracts).
We will explore the blockchain infrastructure layers in detail in a separate article.
SECURITY VULNERABILITIES IN BLOCKCHAIN SYSTEMS
Now that we have a logical idea of the various layer in blockchain, let’s explore some security issues that prevalent in each layer.
Hardware Layer:
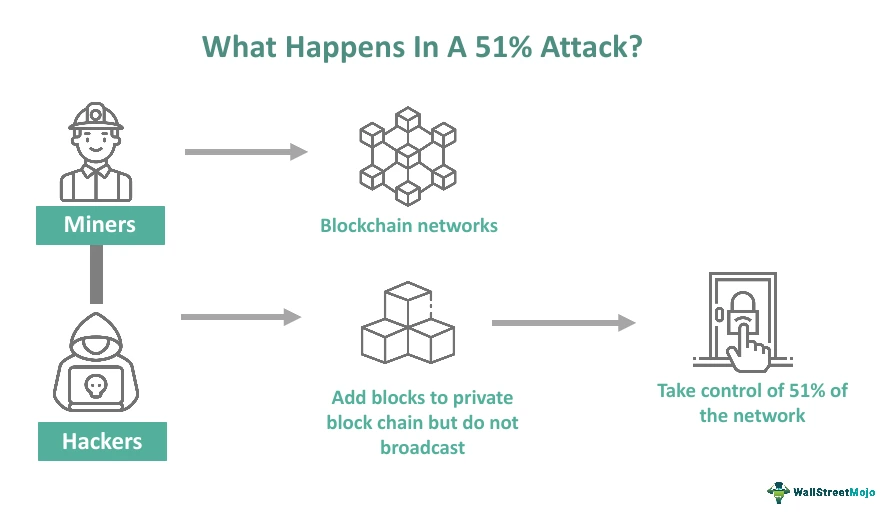
1. 51% attack: This is a major hardware attack where a malicious actor can gain control over half the nodes in a network. Under this condition, the attacker can control the mining power, manipulate transactions, reverse transactions, and also lead to double spending of tokens.
(Source: WallstreetMojo)
2. Mining pool manipulation: This is an attack where the attacker controls the mining power of the network, thereby influencing the performance of the blockchain by changing the hash rate of the network. This attack is a connected to the 51% attack.
3. Hardware Vulnerabilities: These are inherent vulnerabilities that maybe present in the hardware components used as part of mining rigs and mining nodes that could possibly give the attacker an advantage and facilitate unfair mining.
Data Layer:
1. Transaction malleability: is a type of man-in-the-middle attack where a malicious entity can manipulate the contents of a transaction en route to a node. Important details like recipient’s address can be manipulated, leading to loss of funds.
2. Race condition attacks: This attack exploits the timing interval between different transaction. The attacker submits multiple conflicting transaction, thereby affecting the transaction results.
3. Replay attacks: Replaying a previously broadcasted transaction to deceive the network to process it again, hence resulting in double spending.
4. Hash collision attacks: The attacker finds two conflicting data types, which potentially produce the same hash value. This condition could be used for fraudulent data insertion into the block.
5. Data injection attacks: Inject fake or malicious data to alter or corrupt the ledger entries.
Network Layer:
1. Routing attacks: This is a cyberattack that disrupts the communication between nodes. There are two types of routing attacks:
a. Partitioning Attack – where the attacker acts a bridge between two blockchains, and
b. Delay Attacks – here the delivery of a block is delayed to a certain victim node, denying the node details of the block and the transactions within. This results in Denial of Service, double spending and revenue loss.
2. 51% attacks: As mentioned in the hardware layer, Sybil attacks can lead to a 51% attack where a malicious actor/actors gain more than 50% control of the blockchain network, hence impacting the collective consensus of the network.
This impacts the integrity of the blockchain, leading to the chain getting forked into two different chains.
3. Phishing Attacks: Like traditional attacks, phishing attacks are used to lure users into clicking malicious links and installing malicious apps that in turn steal private keys from the users, draining their funds from their crypto wallets.
4. Man-in-the-middle Attacks: This is an interception attack where the bad actor is intercepting the traffic between a user and his crypto wallet.
This again leads to theft of private keys, hence compromising the crypto wallet.
Consensus Layer:
1. 51% attack: This attack shows it effects across the blockchain layers.
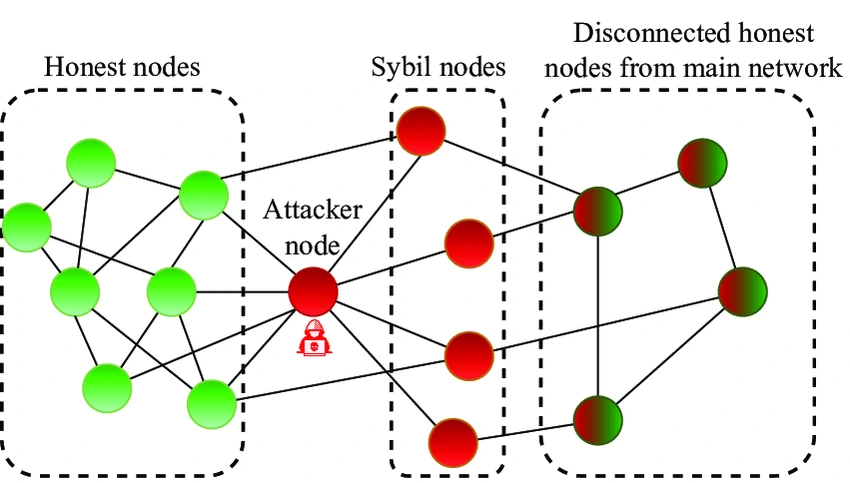
2. Sybil attack: The attacker creates multiple fake identities using a blockchain node to gain influence and control over the network. Once these fake identities have overwhelmed the network, they can be used to isolate a legitimate node and use it to create further fake identities.
This impacts the network by fooling the honest nodes, leaving them incapable of identifying fraudulent transactions. Sybil attacks often lead to 51% attack, which in turn could lead to forking of the network into two separate blockchains.
(Source: ResearchGate)
3. Mining Pool Attack: This attack follows a Sybil attack + 51% attack, where the dominant mining pool compete and controls the consensus of the network.
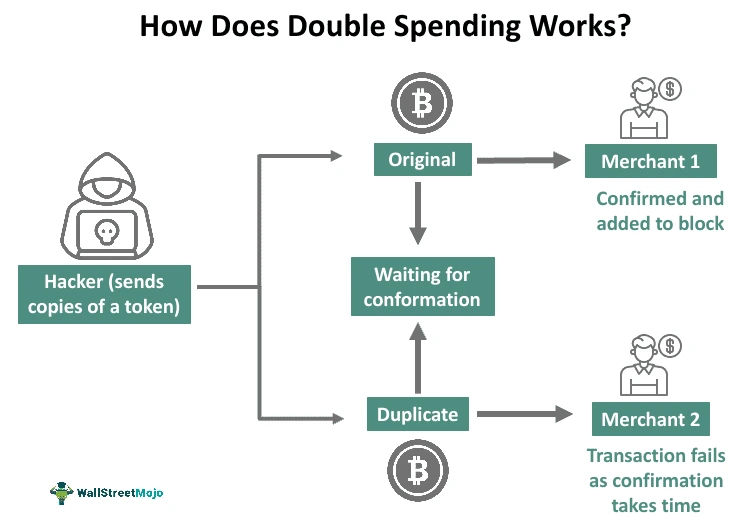
4. Double-spending attacks: Fraudulent transactions where the attacker tries to spend the same coin multiple times. This attack occurs in parallel with a hash condition and race condition attack.
(Source: WallstreetMojo)
5. Routing attacks: This attack is the same as the network layer.
Application Layer:
1. DDoS attacks(Distributed Denial of Service): Flooding a blockchain application with excessive network traffic, thereby paralysing the servers hosting the applications. As a result, legitimate users are denied access to the blockchain application, resulting in a denial of service.
When this attack is carried by several compromised blockchain nodes, it results in a distributed denial-of-service attack.
2. Injection attacks: Injecting malicious code into blockchain dApps that could result in malicious behaviour of the apps. Code injection attacks are often used to carry out
SQL injection attacks (a malicious user is able to carry out unauthorised database queries to steal information) and XSS attacks (Cross-site scripting attacks are server attacks where a code injection could alter the response of web queries sent to the user.)
3. Smart Contract Exploits: Just like application code vulnerabilities, smart contract code vulnerabilities can wreak havoc in a blockchain environment. Smart contract vulnerabilities or exploits can be used to drain funds or inject malicious data, thereby corrupting the ledge with false entries.
(Source: Rapid Innovation)
4. Brute-Force Attacks: As the name implies, this is a disruptive attack in which the attacker uses a database of compromised passwords to repeatedly attempt to guess a legitimate user’s password on a dApp.
We shall revisit blockchain security in the next part of this article, where we will showcase a few famous blockchain hacks and current security measure followed by the industry.
FUTURE-PROOFING YOUR BLOCKCHAIN IMPLEMENTATION
The fast-growing blockchain ecosystem continues to introduce new technological advancements, which also create additional entry points and attack vectors that could be exploited. As a result, blockchain security is advancing rapidly and is set to develop into a specialized practice of its own.
▶ Buy Crypto at Bitget
CoinRank x Bitget – Sign up & Trade to get $20!