KEYTAKEAWAYS
- Permissionless blockchains prioritize open access and decentralization but face scalability and privacy challenges.
- Permissioned blockchains offer controlled access, easier upgrades, and customization, often suited for enterprises and governments.
- Blockchain design is flexible, and real-world systems may combine elements of both permissioned and permissionless models.

CONTENT
What are permissioned and permissionless blockchains? Learn how they differ in access control, governance, scalability, and use cases, and how each model fits different blockchain applications.

WHAT ARE PERMISSIONED & PERMISSIONLESS BLOCKCHAINS?
Blockchains come in different forms, and one of the most important distinctions is whether a blockchain is Permissioned or Permissionless. Understanding this difference helps clarify how a network is governed, who can participate, and what kind of use cases it is best suited for.
📌 Permissionless Blockchains
A Permissionless blockchain is an open network that anyone can access and use. No prior approval is required to join the network, submit transactions, run a node, or participate in the validation process.
These networks are designed to be open by default, allowing public participation while relying on consensus mechanisms to maintain security and integrity.
Well-known examples of Permissionless blockchains include Bitcoin, BNB Chain, and Ethereum.
In each case, the network remains accessible to anyone, with no central authority controlling who is allowed to participate.
📌 Permissioned Blockchains
In contrast, a Permissioned blockchain restricts participation to approved entities. Users or nodes must be granted explicit permission before they can join the network or take part in transaction validation.
Because of this controlled access, Permissioned blockchains are typically used in private or semi-private environments, such as within organizations or enterprise systems.
For example, a company may use Hyperledger Fabric to build a Permissioned blockchain for supply chain management. In this setup, network access is managed by administrators, and only authorized participants are allowed to interact with the system.
>>> More to read: What is Blockchain and How Does It Work?
KEY CHARACTERISTICS & PROS AND CONS
The following characteristics do not apply uniformly to every Permissioned or Permissionless blockchain. However, in most cases, these traits generally reflect the typical design patterns associated with each model.
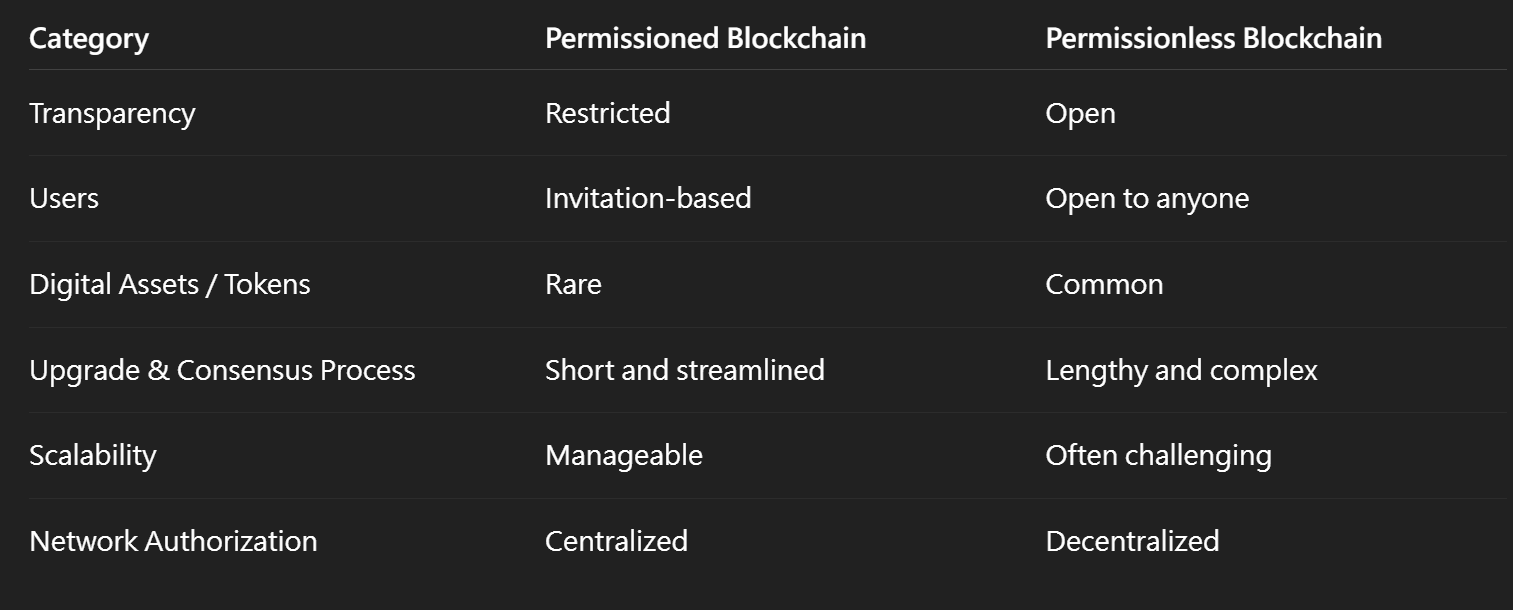
🚩 Permissionless Blockchains: Advantages
▶ Decentralization potential.
Not every Permissionless blockchain is fully decentralized in practice, but most of them offer a high degree of decentralization potential. As long as users are willing and have the necessary resources, anyone can participate in the consensus mechanism or interact with a Permissionless network.
▶ Collective consensus.
Users can voluntarily join the network and take part in decisions regarding protocol changes. Validators and network participants may also express disagreement, and unpopular changes can result in alternative versions of the network through forks.
▶ Ease of access.
Anyone can create a wallet and join a Permissionless blockchain. These networks are generally easy to access, with relatively low barriers to entry compared to controlled systems.
❗Permissionless Blockchains: Disadvantages
▶ Scalability challenges.
Permissionless blockchains must support large user bases and high transaction volumes. Improving scalability typically requires network upgrades, which must be approved through collective consensus before they can be implemented effectively.
▶ Malicious participants.
Because Permissionless blockchains are open to everyone, there is always a risk of malicious actors operating within the network.
▶ Excessive transparency.
Most information on Permissionless blockchains is publicly accessible. While this supports openness, it may also introduce potential privacy and security concerns.
🚩 Permissioned Blockchains: Advantages
▶ Scalability.
Permissioned blockchains are usually operated by identifiable entities and maintain a degree of control over validators. As a result, implementing upgrades is generally easier and more efficient.
▶ Customization.
A Permissioned blockchain can be designed for specific purposes and optimized for particular functions. When changes are required, the system can be modified with relative ease.
▶ Controlled transparency.
Operators of Permissioned blockchains can determine the appropriate level of transparency based on the intended use case.
▶ Invitation-based access.
A Permissioned blockchain allows precise control over who is allowed to join the network and who is excluded.
❗ Permissioned Blockchains: Disadvantages
Centralization.
Control may rest with a central entity or a small group of validators selected by the blockchain owner. This means network decisions may not reflect the interests of all stakeholders.
Increased vulnerability to attacks.
Permissioned blockchains often rely on a limited number of validators, which can make their consensus mechanisms less resistant to attacks.
Censorship risk.
Network connections or updates introduced by Permissioned blockchain operators may introduce censorship risks. If enough participants agree, information stored on the blockchain could potentially be altered.
>>> More to read: 6 Common Types of Blockchain Consensus Mechanisms
SHOULD YOU USE A PERMISSIONED OR PERMISSIONLESS BLOCKCHAIN?
The answer to this question is relatively straightforward. If your goal is to build a service that is open to everyone, then a Permissionless blockchain is the appropriate choice. However, using a Permissionless blockchain does not mean you must strictly follow the conventional principles or ideological goals often associated with public networks.
In practice, it is possible to design a blockchain that is Permissionless yet still centralized in its operation. Depending on your objectives, you can also incorporate additional privacy features while maintaining open access at the network level.
If, on the other hand, you plan to use blockchain technology in a private environment—such as within an enterprise or a government setting—a Permissioned blockchain is generally more suitable. That said, a Permissioned blockchain does not have to conform to every commonly assumed characteristic of permissioned systems. It can still be fully transparent and even allow public visibility, depending on how it is designed and governed.
✏️ Summary
Even if, as a crypto investor, you primarily interact with Permissionless blockchains, understanding the differences between Permissioned and Permissionless blockchains is highly valuable. It is easy to assume that distributed ledger technology (DLT) naturally aligns with transparent, open, and decentralized cryptocurrency models.
However, these assumptions do not always hold. In reality, many private organizations actively use Permissioned blockchains that intentionally deviate from traditional expectations. This flexibility highlights an important point: blockchain design is not binary, and real-world implementations often blend characteristics from both Permissioned and Permissionless models to meet specific needs.

















